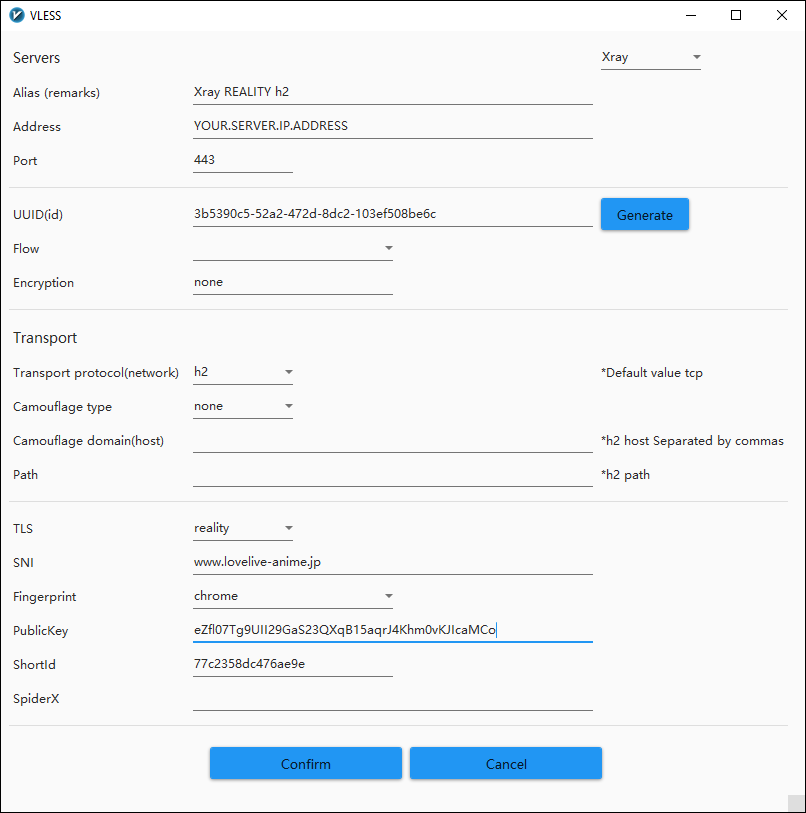
Xray REALITY h2
Server
You will need a small virtual private server (VPS).
Install Xray-core on your server using https://github.com/XTLS/Xray-install. For example, to get the latest beta and configure it to run as root:
1 | bash -c "$(curl -L https://github.com/XTLS/Xray-install/raw/main/install-release.sh)" @ install --beta -u root |
Configure the server using the example from https://github.com/chika0801/Xray-examples/blob/main/VLESS-H2-uTLS-REALITY/config_server.json.
The example provides comments on certain attributes in the JSON configuration file for the Xray server:
| Attribute | Value |
|---|---|
id |
Do xray uuid to generate an id, or use any 1-30 byte string |
flow |
Leave blank |
show |
If set to true, the program will output debug information |
dest |
The minimum standard of the destination website is that it be a foreign website, support TLSv1.3, X25519, and H2, and the domain name not be redirected (although the main domain name may be redirected to the www subdomain). |
serverNames |
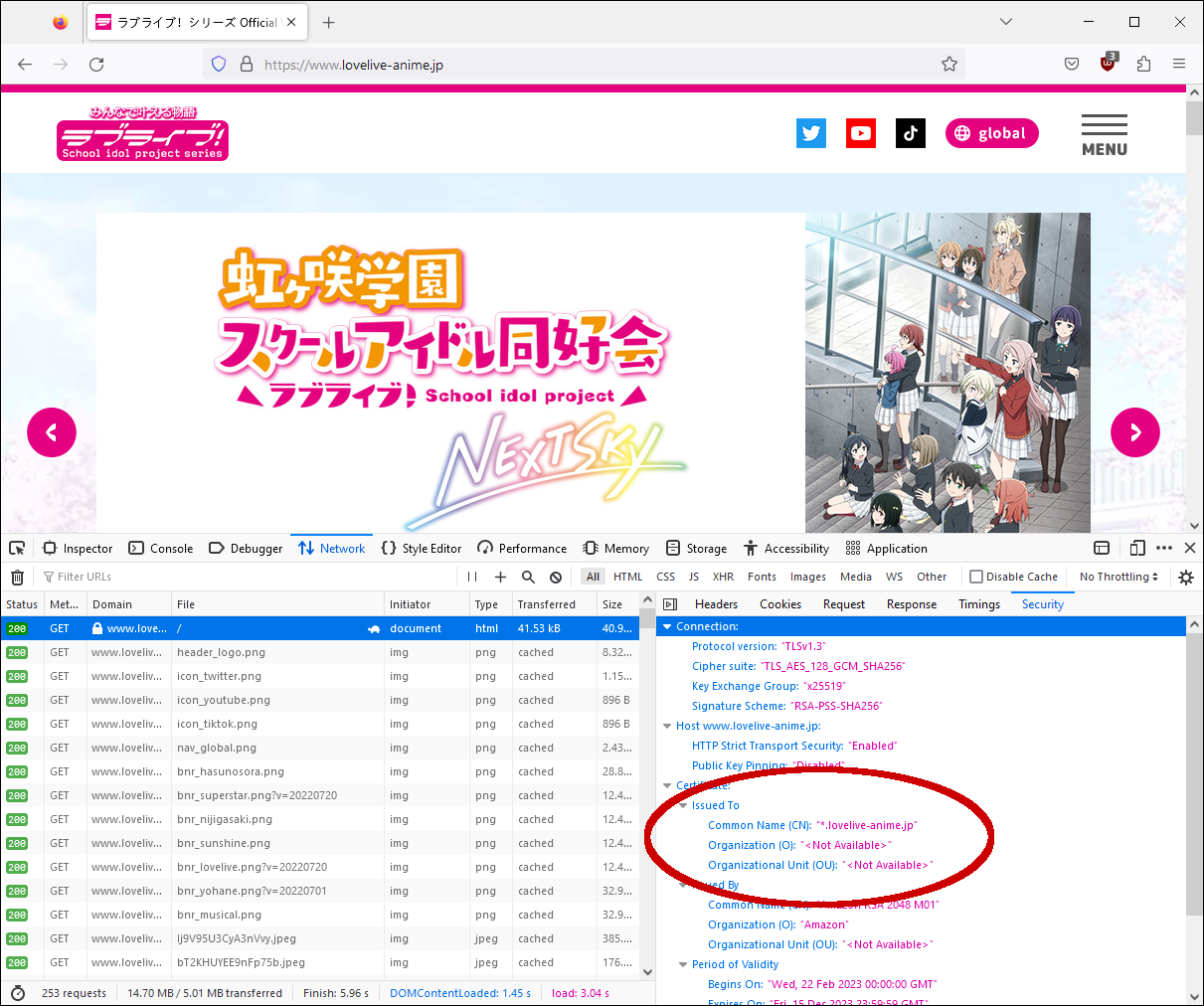
The serverName list available to the client. Wildcards * are not supported yet. The server name must match the name on the site’s SSL certificate. You can check the destination site’s SSL certificate details in the developer tools section of your browser. |
privateKey |
Execute xray x25519 for generation, and fill in the value of Private key here |
shortIds |
A list of the shortId available to clients, which can be used to distinguish different clients. Each shortId consists of hexadecimal characters 0 through f. The length is a multiple of 2. The upper limit of the length is 16. The value can be left blank, or execute openssl rand -hex 8 to generate a value. |
Example of id generation:
1 | xray uuid |
Results:
1 | 3b5390c5-52a2-472d-8dc2-103ef508be6c |
Example of checking destination site’s SSL certificate details in the developer tools section of a browser:
Example of public key generation:
1 | xray x25519 |
Results:
1 | Private key: QNraK6EdxPNOzfbL2G1BTl_OeMSxm49H5vps2qzQ3E0 |
Example of shortId generation:
1 | openssl rand -hex 8 |
Results:
1 | 77c2358dc476ae9e |
Example of a completed server configuration file /usr/local/etc/xray/config.json:
1 | { |
Restart xray systemd service with your final configuration file:
1 | systemctl restart xray |
Results:
1 | xray.service - Xray Service |
Client using CLI
You can get command-line interface clients from https://github.com/XTLS/Xray-core/releases.
You can configure the CLI client using the example from https://github.com/chika0801/Xray-examples/blob/main/VLESS-H2-uTLS-REALITY/config_client.json.
The example provides comments on certain attributes in the client configuration:
| Attribute | Value |
|---|---|
address |
IP of the server |
id |
Consistent with the server |
flow |
Leave blank |
fingerprint |
Emulate client-side TLS fingerprinting using the uTLS library |
serverName |
Consistent with the server |
publicKey |
On the server execute xray x25519 to generate the public key and private key, and then on the client fill in the value of Public key here |
shortId |
Consistent with the server |
spiderX |
The initial path and parameters of the crawler are recommended to be different for each client |
Example of a completed client configuration file config.json:
1 | { |
Run the CLI client with the above configuration file.
Client using GUI
Get your Windows client software from https://github.com/2dust/v2rayN.
The latest version is https://github.com/2dust/v2rayN/releases/download/6.27/v2rayN-With-Core.zip.
Unzip the zip file.
If you want to be sure of having the very latest Xray core, then download the Xray core for Windows 64-bit from https://github.com/XTLS/Xray-core/releases, unzip it, and copy xray.exe into Downloads\v2rayN-With-Core\v2rayN-With-Core\bin\Xray replacing the existing xray.exe.
You can check which version you have by opening a command prompt in that folder and issuing the command:
1 | xray --version |
Example of results:
1 | Xray 1.8.3 (Xray, Penetrates Everything.) Custom (go1.20.5 windows/amd64) |
Launch the v2rayN application.
Click the v2rayN icon in the Windows system tray to bring up the GUI.
Configure the v2rayN GUI for a new VLESS server, using the same values as went in the configuration JSON file for the CLI client: