OpenVPN through Hysteria2
Linux server
You will need a server, a domain name, and a hostname DNS A record (or AAAA or IPv6). Our example domain name will be example.com, and our example hostname will be vps5.example.com.
Open ports tcp/80, tcp/443, and udp/443 in the server firewall. Note that Hysteria uses UDP.
Update server:
1 | apt update && apt upgrade -y |
Download the OpenVPN install script from https://github.com/angristan/openvpn-install:
1 | curl -O https://raw.githubusercontent.com/angristan/openvpn-install/master/openvpn-install.sh |
Then run it:
1 | ./openvpn-install.sh |
When prompted, specify your server public IP address. You can use the default port of udp/1194. This need not be open in your server firewall, since traffic arrives via Hysteria.
Give your first client a name, e.g. windows. The client configuration file is written to /root/windows.ovpn (in this example).
The OpenVPN install script opens port udp/1194 in iptables. If you want to further conceal your server, close this port by manually editing /etc/iptables/add-openvpn-rules.sh and /etc/iptables/rm-openvpn-rules.sh. Remove the lines for udp/1194 in both files. Then reboot.
Install Hysteria on the server using the script provided by the Hysteria developers:
1 | bash <(curl -fsSL https://get.hy2.sh) |
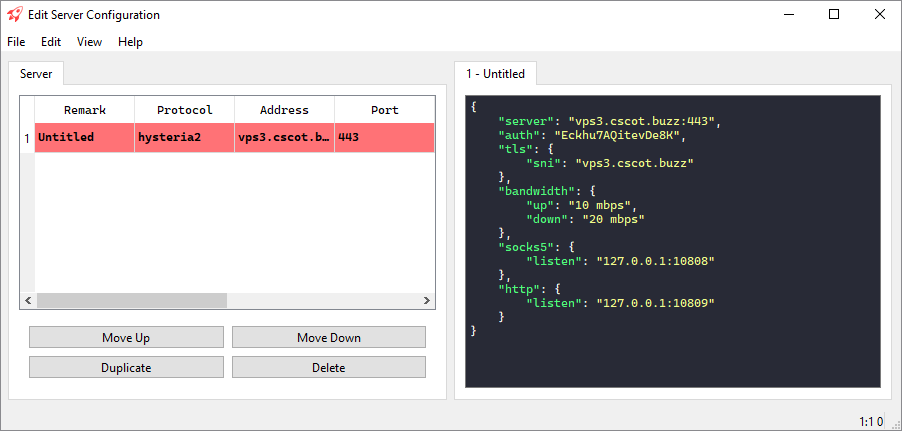
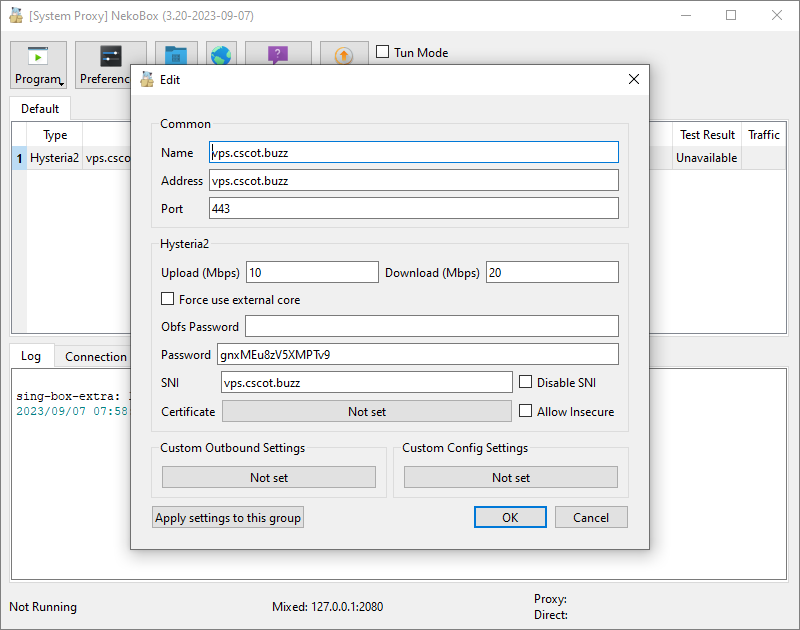
Edit the server configuration file at /etc/hysteria/config.yaml using an editor such as vi or nano. Specify your server hostname, your email, and your choice of password (or use the default generated by the install script). Optionally you can also change the masquerade URL. See the Hysteria2 documentation.
1 | # listen: :443 |
Save the file.
Optionally set the log level by editing the file /etc/systemd/system/hysteria-server.service:
1 | Environment=HYSTERIA_LOG_LEVEL=debug |
If you make this change, then after saving the file also do:
1 | systemctl daemon-reload |
Start your Hysteria server with:
1 | systemctl start hysteria-server |
Configure Hysteria to start on system boot with:
1 | systemctl enable hysteria-server |
You can view the server log at any time with:
1 | journalctl -u hysteria-server |
Windows client
Download the latest Hysteria for Windows from https://github.com/apernet/hysteria/releases. The file you need for most Windows PCs will be hysteria-windows-amd64.exe.
Create a configuration file config.yaml in the same directory as hysteria-windows-amd64.exe, which by default will be Downloads.
Make the client config.yaml match your server address and password, and your bandwidth capabilities. For example:
1 | server: vps5.example.com:443 |
See the documentation for details of the client configuration file.
Open a Command Prompt window and change into your Downloads directory.
1 | cd Downloads |
Optionally set the log level:
1 | set HYSTERIA_LOG_LEVEL=debug |
Start the program with the configuration file config.yaml:
1 | .\hysteria-windows-amd64.exe |
Leave the Command Prompt window open with Hysteria running in it.
You can view the client log at any time by looking at the Command Prompt window.
Open a PowerShell window. Securely download the generated client configuration file from the server, e.g.:
1 | scp root@vps5.example.com:/root/windows.ovpn Downloads |
Edit the file Downloads/windows.ovpn in an editor such as Notepad or Notepad++.
Make it look as if the remote server is on localhost by changing the remote line to read:
1 | remote 127.0.0.1 1194 |
Also insert these two lines, replacing YOUR.SERVER.IP.ADDRESS by your actual server IP address:
1 | route YOUR.SERVER.IP.ADDRESS 255.255.255.255 net_gateway |
Save the file.
If you have not already done so, install the OpenVPN GUI client for Windows from https://openvpn.net/community-downloads.
Import the amended client configuration file Downloads/windows.ovpn into the OpenVPN GUI.
Connect the OpenVPN client to the OpenVPN server.