Xray WireGuard output to Cloudflare WARP
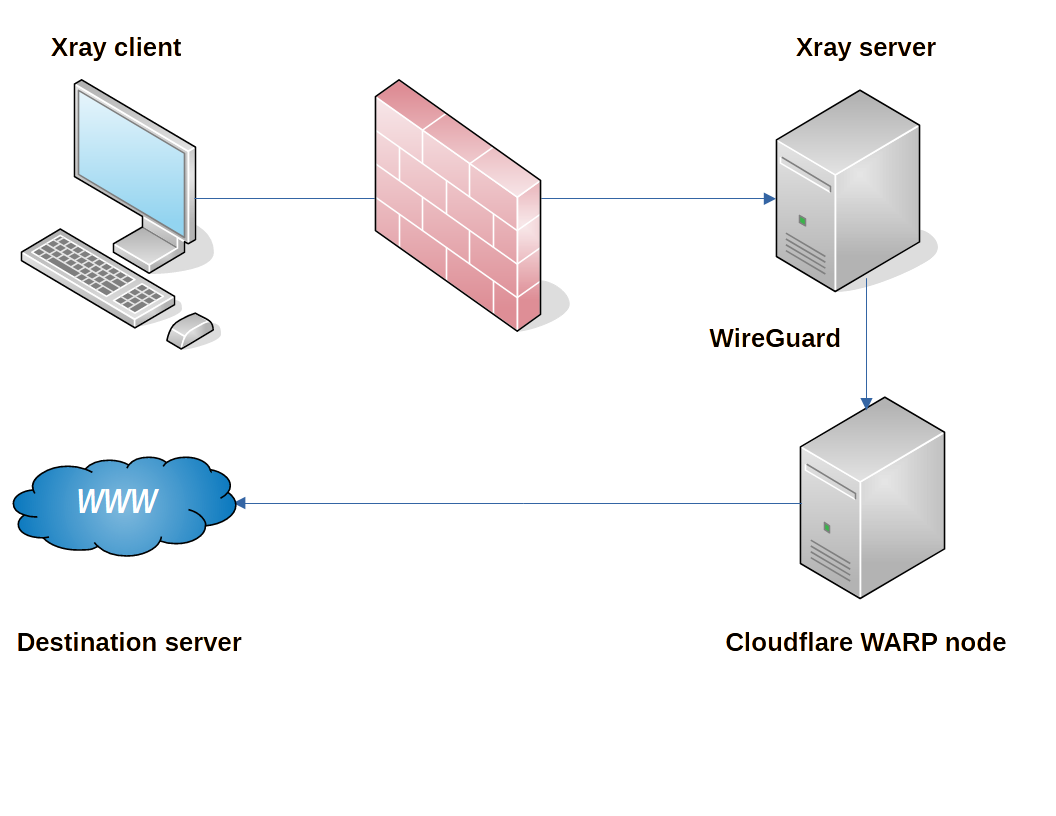
Xray offers WireGuard as a outbound protocol possibility.
This feature is not intended for tunneling through a firewall. WireGuard is too easy to detect.
Rather it is intended to provide you with the possibility of diverting your outbound traffic through Cloudflare. By routing your traffic (in WireGuard protocol) to a free Cloudflare node, your traffic will reach its final destination from an IP address different from your server’s IP address.
This is especially important for traffic that returns to your own country. You do not want packets to go out and return directly from the same IP address. That would make it obvious that your server is a proxy server.
Rather you divert such packets through Cloudflare. That way they come back to your country from an anonymous-looking Cloudflare WARP IP address.
(WARP is Cloudflare’s VPN service. Using WARP, you connect to the Internet through Cloudflare’s servers, optimizing your traffic along the way.)
The stages in configuring Xray to divert traffic through Cloudflare WARP servers are:
- Register for a Cloudflare WARP account, which in the process generates a Cloudflare WARP configuration.
- Export your Cloudflare WARP configuration in sing-box format.
- Use your WARP configuration to add a new outbound from your Xray server that routes traffic through Cloudflare WARP using the WireGuard protocol.
- Add routing instructions that determine which packets are to be diverted through Cloudflare WARP.
For a detailed example see https://github.com/chika0801/Xray-examples/blob/main/wireguard.md.